Recent Articles
How To Recover Overwritten Files
The Snowflake Data Breach: A Comprehensive Overview
Mac Not Recognizing External Hard Drive: Quick Fix Solutions
How Multi-Cloud Backup Solutions Can Prevent Data Disasters
Capibara Ransomware: What is it & How to Remove
What Should a Company Do After a Data Breach: The Ticketmaster Incident
Secles Ransomware: Removal Guide
What To Do When Your Chromebook Freezes
How to Create Hyper-V Backup
What Is The Best Data Recovery Software For PC
I think there's an issue with my storage device, but I'm not sure Start a free evaluation →
I need help getting my data back right now Call now (800) 972-3282
The effects of a ransomware attack on businesses or personal data are costly. To prevent ransomware attacks, users must improve their cyber security measures.
Ransomware is a type of malware, a malicious program used to infect systems and steal data. Most ransomware will encrypt the files, exfiltrate sensitive and critical data, and then threaten to leak or destroy the data unless a ransom is paid. Hackers usually determine a time for businesses to contact them. If the victims fail to contact them, then they leak the data.
Just in the last few years, ransomware attacks increased drastically in number and became more sophisticated as well. With most people working from home, businesses had to improve their cybersecurity solutions to prevent vulnerabilities that hackers explore to steal data.
In our expert experience, the investment in cybersecurity and prevention does not compare to the costs of working on ransomware removal and recovery.
15 Tips for staying protected from ransomware attacks
By staying up-to-date with the latest ransomware trends and threat intelligence, you can better understand potential risks and develop effective countermeasures, ultimately minimizing damage and ensuring a quicker recovery in case of an attack.
Here is a list of solutions to protect your business from ransomware attacks:
1. Apply cyber security protocols and train employees
Training employees on cybersecurity is essential to prevent cyber attacks, including ransomware. Invest in employee training and make cybersecurity awareness a priority in the company’s culture. Teach employees how to spot phishing emails, make strong passwords, know when and how to report a security breach, and understand the best security practices for workstations.

Use security software as well, such as installing ad blockers on all employee devices and browsers to avoid malicious marketing that can trick users into downloading and installing ransomware. Harden endpoints by configuring access controls and implementing multi-factor authentication and strong password requirements.
Also, segment your network to limit the spread of ransomware. Not only that, but also use a firewall to protect your network, and regularly monitor and patch your systems to ensure your network security.
2. Keep all systems and software updated
Many hackers and ransomware gangs exploit known vulnerabilities in software to infect networks and steal businesses’ data.
By keeping your software and operating system (OS) updated, you can prevent these types of attacks, known as Zero-day attacks.
3. Set unique passwords and multifactor authentication
Passwords must be unique for each account and have a mix of letters, numbers, and special characters. This will make it hard for hackers to guess the password and enter the system or account. Besides, passwords with 15 or more characters also increase security since it makes it harder for hackers to guess them.
Strong password management tools are essential to mitigate the risks of cyber-attacks and data leaks for both small and medium enterprises. A password manager is a computer program that allows users to store and manage their passwords for local applications or online services such as web applications, online shops, or social media. Password managers typically require a user to create and remember one “master” password to unlock and access all the stored passwords.
Also, setting a multifactor authentication (MFA) to every account and VPN connection. This will prevent unauthorized access to them, adding extra protection against cyber threats.
4. Install antivirus software and firewalls
Antivirus, anti-malware, and firewalls will block unauthorized access to the computer. Also, they alert potential malicious websites and email attachments.
In addition, these security programs can quarantine threats and scan the machine for malicious files.
Remember to keep your security software updated and to set regular scans to ensure no malware enters the system.
5. Only install software or applications from official sources
Efficient and highly secure software can be expensive, due to the extensive research & development, as well as the regular security patches and updates provided. This helps ensure that hackers can’t exploit vulnerabilities.
However, using free illegal versions puts your machine in danger of being hacked. It can also leave open backdoors that cybercriminals exploit. Besides, many ransomware are disguised as pirated software so victims install them unaware.
6. Apply network segmentation
The Principle of Least Privilege (POLP) to all systems and services means restricting users to only having the access they need to perform their jobs. Network segmentation ensures that only authorized personnel can access specific data. This increases sensitive and critical data security. That is because, in case of a ransomware attack, it will not be able to spread across the network.
Network segmentation is the process of dividing a larger network into smaller sub-networks with limited interconnectivity between them. By controlling traffic flows between various sub-networks and by restricting attacker lateral movement, network segmentation prevents unauthorized users from accessing the organization’s intellectual property and data.
By segmenting the network, companies can prevent attackers from moving laterally across the network, limiting the impact of a ransomware attack. For example, if a ransomware attack infects one segment of the network, it may not be able to spread to other segments, reducing the overall impact of the attack
7. Backup data regularly
Effectively backing up your files essentially means that you never have to start from scratch in the event of a data breach or ransomware attack.
Ensure you’re following the 3-2-1 backup rule, where at least one encrypted backup copy is stored offline and offsite. This way, no cyber attackers will successfully breach your backup and you can use it in case of any type of incident or disaster, including ransomware.
In addition, you should also aim to create backups at least weekly.
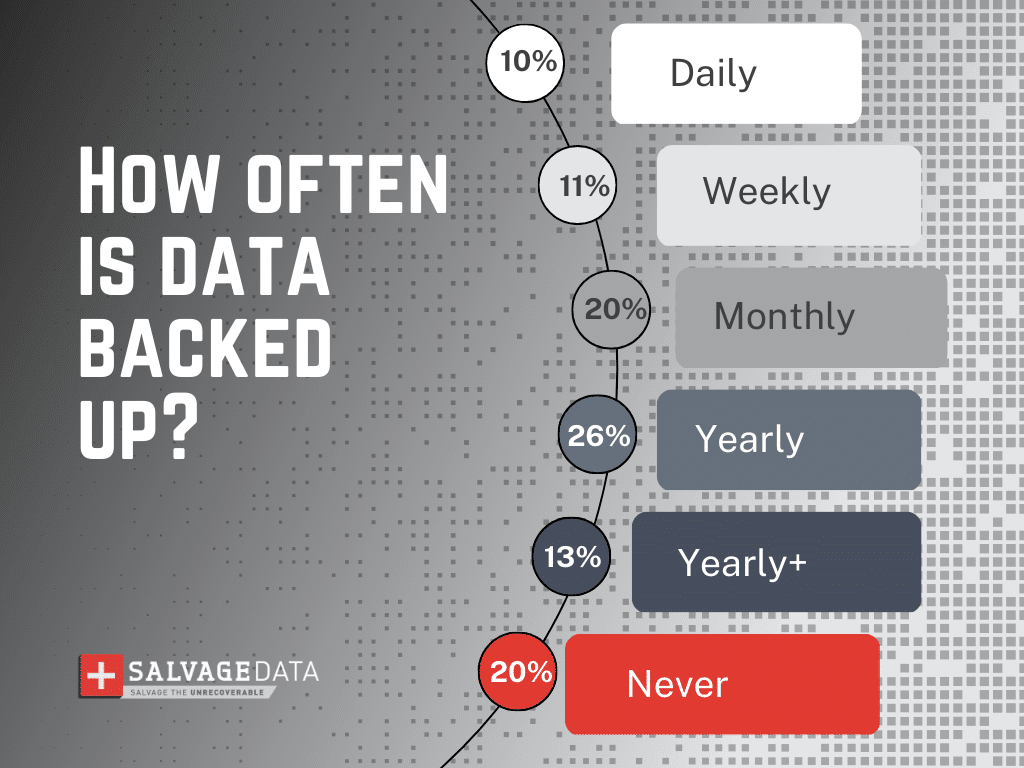
Source: The 2022 Backup Survey by Backblaze.
8. Use email protection
Spam filters and email protection software can prevent phishing emails from reaching your employees. To apply this solution, install and configure spam filters and email protection software on all devices and networks.
For example, content filters on mail servers can reduce the risk of spam with malicious attachments or infected links reaching your mailbox. As well, Ad blockers can prevent malicious marketing that can trick users into downloading and installing ransomware.

Plus, educate employees on the various risks associated with cyber-attacks and how to protect against them. Teach employees how to spot phishing emails, make strong passwords, know when and how to report a security breach, and understand the best security practices for workstations.
9. Harden endpoints
An endpoint is a connection point in a communications network that serves as a node or a device that performs a specific function. It is an autonomous device that exchanges data and resources with other endpoints in a network.
Endpoints can be computers, servers, laptops, smartphones, tablets, or any other computing device used to connect to and communicate on a network.
Endpoints can be hardened by using:
- Antivirus and malware protection
- Secure passwords
- Restricting internet access
- Using endpoint security solutions
- Enabling regular scans
- Implementing Software Restriction Policies (SRP)
- Keeping all systems and software updated
10. Develop ransomware plans and policies
Developing ransomware plans and policies is a critical step in preventing ransomware attacks.
It includes developing an incident response (IR) plan that guides your IT and security teams during a ransomware event. Your IR plan should include roles and communications. Which should be shared during an event and a list of contacts (like partners or vendors) that must be notified.
Also, take a layered approach to security by using more than one security tool. That can be a combination of a firewall, antivirus software, anti-malware software, spam filters, and cloud data loss prevention.
11. Regularly run vulnerability & penetration testing
The best way to test your company’s security is to try to break it with regular security audits and vulnerability assessments. This can help identify any weaknesses in the company’s security infrastructure and allow for proactive measures to be taken to address them before attackers can exploit them.
A step further is hiring a penetration testing service. This is a simulated attack that is performed by security experts who apply various hacker-like tactics in order to uncover potential entry points into the system and determine the best mitigation techniques.
12. Apply Zero Trust Architecture
Zero Trust Architecture is a security model that can help prevent ransomware attacks. This approach is based on the principle of “never trust, always verify.” It assumes that all devices, users, and applications are untrusted and must be verified before being granted access to sensitive data.
To apply Zero Trust Architecture to prevent ransomware, organizations need to adopt a security model that can accommodate a distributed workforce and remote work culture. This model should protect devices, applications, and data irrespective of their location.
The guiding principles of Zero Trust Architecture include:
- Continuous verification
- Segmentation
- Least privilege access
- Authentication
- Monitoring
Endpoint devices are continuously monitored for malicious activity, malware, or network access requests initiated from a compromised endpoint. This helps detect and prevent ransomware attacks before they can cause damage.
By carefully monitoring all network activities, companies can detect and respond to ransomware attacks in real-time. This can help limit the damage caused by an attack.
An identity and access management (IAM) product should be put in place to allow users and their rights or permissions to be authenticated. This helps ensure that only authorized users have access to sensitive data.
13. Use Infrastructure as Code (IaC)
Infrastructure as Code (IaC) is a process of managing and provisioning IT infrastructure through machine-readable definition files, rather than physical hardware configuration or interactive configuration tools.
The IT infrastructure managed by this process comprises both physical equipment, such as bare-metal servers, as well as virtual machines, and associated configuration resources.
The ability to treat infrastructure as code and use the same tools as any other software project would allow developers to rapidly deploy applications.
To use Infrastructure as Code (IaC), organizations need to adopt a code-based infrastructure automation process. This involves configuring and managing the infrastructure through a descriptive model, treating infrastructure configuration, and provisioning the same way as the application source code.
Infrastructure as Code (IaC) can be used to prevent ransomware attacks by deploying and updating cloud resources and keeping backups. To prevent ransomware attacks, collaboration between infrastructure and security teams is crucial to ensuring an organization’s readiness against ransomware attacks. Jointly assessing and improving security and recovery processes can enhance an organization’s recoverability.
14. Update cloud resources
Updating cloud resources is one of the ways to prevent ransomware attacks. This is because Cloud services retain previous versions of files, which allows you to roll back to an unencrypted version in case of an attack.
Keeping all systems and software updated, installing antivirus software, upholding your firewall, having network segmentation, email protection, data encryption, IAM, and identifying misconfigurations in your cloud environment are also best practices to prevent ransomware attacks.
15. Secure domain controllers (DCs)
Secure domain controllers (DCs) are Windows Server roles that house Active Directory Domain Services (AD DS). They are a common target for attackers in Active Directory ransomware attacks. That is because they contain the credential store for all the user and computer accounts used to secure resources across the enterprise.
In a typical Active Directory ransomware attack, bad actors attempt to gain network access by fishing for user credentials, escalating privileges, and moving vertically into the server network. The end goal is to obtain administrative access rights and compromise a domain controller.
If an attacker is successful, they essentially own the network and gain access to all its various servers and data.
Domain controllers host a copy of the Active Directory Domain Services (AD DS). Which is a schema with all the objects Active Directory stores and delivers authorization and authentication services for.
To protect Active Directory from ransomware attacks, companies can avoid adding Domain Users to the Local Administrator Group, secure domain controllers, and enable Extended Protection for Authentication (EPA).
Summary
Additional tips for preventing ransomware attacks include disabling macros in Office documents, limiting user access rights, implementing application whitelisting, and regularly monitoring and auditing your network. It’s also crucial to conduct vulnerability assessments and penetration tests. As well as stay informed about emerging threats, use a secure DNS service, and encrypt sensitive data. These measures help minimize the risk of ransomware infection. In addition, they make it more difficult for attackers to exploit any accessed information.

Developing an incident response plan and fostering a security-aware culture within the company are essential steps in ransomware prevention. Encourage employees to report suspicious activities and promote a security-conscious mindset throughout the organization.
We recommend setting up an Incident Response Retainer with a trusted provider, such as SalvageData. This is a service agreement with a cybersecurity provider that allows organizations to get external help with cybersecurity incidents. It provides organizations with a structured form of expertise and support through a security partner, enabling them to respond quickly and effectively in the event of a cyber incident.












