Recent Articles
How To Recover Overwritten Files
The Snowflake Data Breach: A Comprehensive Overview
Mac Not Recognizing External Hard Drive: Quick Fix Solutions
How Multi-Cloud Backup Solutions Can Prevent Data Disasters
Capibara Ransomware: What is it & How to Remove
What Should a Company Do After a Data Breach: The Ticketmaster Incident
Secles Ransomware: Removal Guide
What To Do When Your Chromebook Freezes
How to Create Hyper-V Backup
What Is The Best Data Recovery Software For PC
I think there's an issue with my storage device, but I'm not sure Start a free evaluation →
I need help getting my data back right now Call now (800) 972-3282
In cybersecurity, Incident Response Plan is a term that describes the process by which an organization handles a data breach or cyberattack. Including how the organization identifies, contains, and eliminates cyberattacks.
The goal of Incident Response is to prevent cyberattacks before they happen and to minimize the damage if they do occur.
Incident Response is a set of information security policies and procedures that enable an organization to quickly detect and halt attacks, minimizing damage and preventing future attacks of the same type.
What is a network incident response?
Network Incident Response is a process that includes preparing for, detecting, containing, and recovering from a data breach. It is an overall business function that helps ensure an organization can make quick decisions with reliable information.
The instructions of an Incident Response Plan help the IT staff detect, respond to, and recover from network security incidents.
Network Incident Response is a process that includes seven phases:
- Preparation
- Identification
- Containment
- Eradication
- Recovery
- Lessons Learned
- Test
The 7 phases of incident response
The seven phases of incident response are Preparation, Identification, Containment, Eradication, Recovery, Lessons Learned, and Test.
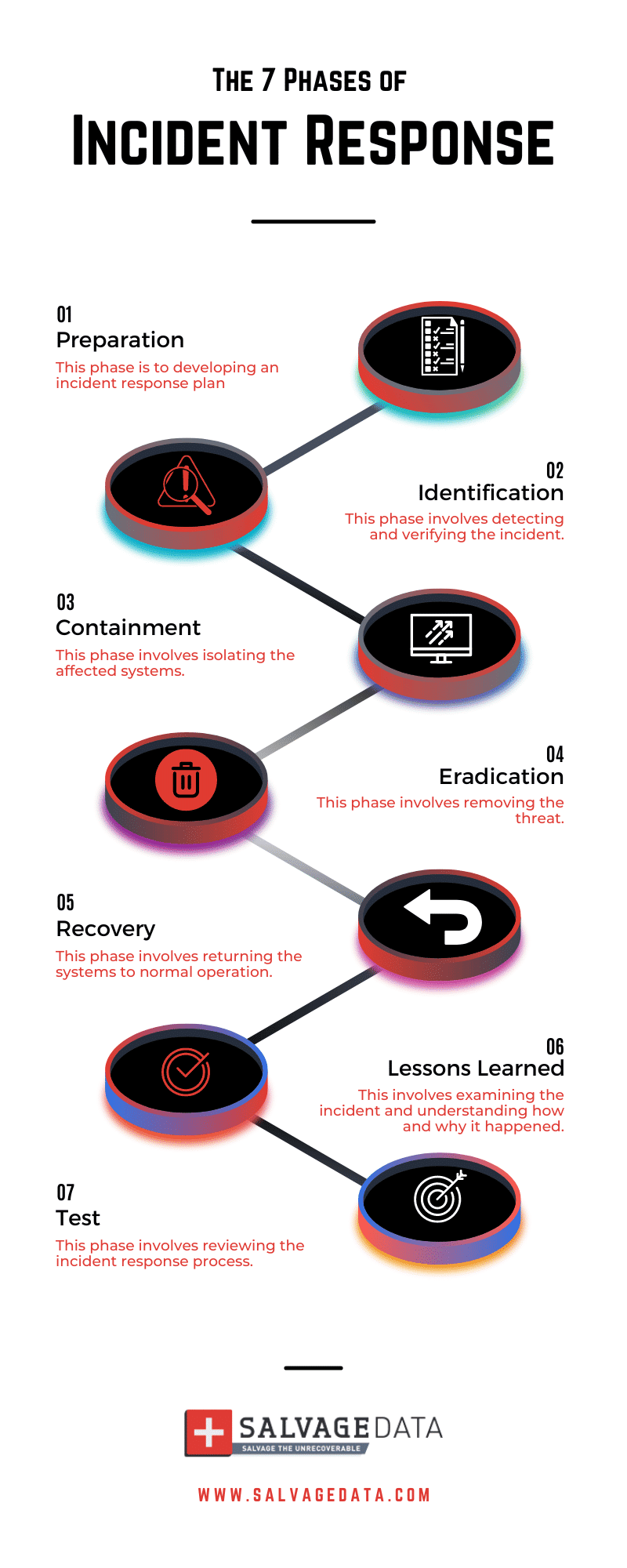
The Preparation phase involves developing an incident response plan. The Identification phase involves detecting and verifying the incident. The Containment phase involves isolating the affected systems and preventing further damage.
The Eradication phase involves removing the threat and restoring the affected systems to their normal state. The Recovery phase involves returning the systems to normal operation and ensuring that the incident does not recur. The Lessons Learned involves examining the incident and understanding how and why it happened. The Test phase involves reviewing the incident response process and making improvements to the incident response plan.
1. Preparation
The Preparation phase of an Incident Response Plan is one of the most essential steps. That’s because it determines how the Incident Response (IR) team will respond to a myriad of incidents that may occur.
Organizations must have policies and procedures for incident response management and enable efficient communication channels. This is what the preparation phase is about.
The Preparation phase includes steps taken before an incident occurs, such as:
- Creating a response team
- Setting a communication channel
- Training in cybersecurity best practices
- Prevention procedures
- Writing incident response policies and procedures
- Providing the necessary tools and resources to the IR team
2. Identification
The Identification phase of an Incident Response Plan involves determining whether an organization has been breached and which type of cyberattack occurred.
It is not always clear at first whether a breach or other security incident has occurred, so it is important to have a process in place to identify and document any potential incidents.
The Identification phase involves completing penetration testing, which is a simulated attack on the organization’s system to evaluate its security and understand the likelihood of a real attack.
The goal of the Identification phase is to quickly identify and contain the incident to minimize the damage to the organization.
3. Containment
The purpose of this phase is to isolate the affected systems and prevent the incident from spreading to other parts of the organization’s network.
During this phase, the IR team will take steps to contain the incident, such as:
- isolating affected systems from the network
- disabling user accounts
- blocking network traffic
The goal of the Containment phase is to limit the damage caused by the incident and prevent it from spreading further while allowing the organization to continue its normal operations as much as possible.
It’s important to remember to not delete the malware so the response team can investigate it and recover the files later.
4. Eradication
The Eradication phase of an Incident Response Plan is the process of actually getting rid of the issue on the affected computer, system, or network. The goal of the Eradication phase is to ensure that the threat is completely removed from the organization’s network and that the affected systems are restored to their normal state.
One of the challenges in the Eradication phase is to ensure that all threats are completely removed from the organization’s network. It is important to choose the eradication approach that is most appropriate for the threat, such as removing malware, patching vulnerabilities, or replacing hardware.
Another challenge is to ensure that the eradication process does not cause any further damage to the organization’s systems. It is important to have a well-documented process in place to ensure that the eradication process is carried out effectively and efficiently.
5. Recovery
The Recovery phase of an Incident Response Plan is the process of restoring the affected systems to their normal state after the threat has been eradicated. The goal of the Recovery phase is to ensure that the organization’s systems are fully functional and secure.
The activities in the Recovery phase include:
- Reinstalling software
- Restoring data from backups
- Testing the systems to ensure that they are functioning properly
Contacting a data recovery service is the most effective way to restore your files lost during an incident or cyberattack.
6. Lessons Learned
The Lessons Learned phase involves examining the incident and understanding how and why it happened. The goal of this phase is to identify areas for improvement in the organization’s security posture and Incident Response Plan.
It includes a review of the incident response process, the effectiveness of the response, and the identification of any gaps or weaknesses in the organization’s security posture.
The Incident Response team should document the lessons learned and use them to update the Incident Response Plan and improve the organization’s security posture.
7. Test
The Test phase of Incident Response involves ongoing testing of assets across the organization to ensure that the incident has been fully resolved.
Incident response testing determines whether you should use an in-house or outsourced incident response process. It also identifies critical gaps. Successful tests allow you to resume operations faster, minimizing or even eliminating downtime. It is important to remember that the incident recovery process is an ongoing cycle, and the preparation phase remains one of the most important steps in the process.
The steps involved in incident response testing include:
- Checklists
- Walk-throughs
- Tabletop exercises
- Simulations (parallel or full interrupt)
Incident response plan testing should engage all relevant internal and external stakeholders to ensure a common understanding of incident response goals, strategies, and best practices. Successful tests lead to resumed operations and service delivery.
Testing and follow-up phases can also be used to collect threat intelligence to guide future incident response testing and exercises. Implementing best practices for incident response testing will provide assurance that the organization is prepared to handle a security incident.
A successful incident response test helps organizations identify attacks, limit the scope of damages, and eradicate the root cause of the incident.
How to implement an incident response plan
To implement an incident response plan, an organization should follow these steps:
- Create a policy. This crucial document is the basis for all incident-handling activities. It provides the IR team with the authority they need to make decisions. The policy should be approved by senior executives and communicated to all employees.
- Establish an incident response team. Identify and train a team of incident responders who will be responsible for executing the incident response plan. The team should include representatives from IT, security, legal, and other relevant departments.
- Develop an incident response plan. Create a document (such as DRP) that outlines the procedures, steps, and responsibilities of the incident response program. The plan should include details on how incident response supports the organization’s broader mission, the organization’s approach to incident response activities required in each phase of incident response, and how the plan aligns with the organization’s priorities and level of acceptable risk.
- Test the plan. Conduct regular tests and exercises to ensure that the incident response plan is effective and up-to-date. This will help identify any gaps or weaknesses in the plan and allow improvements.
- Review and update the plan. Regularly review and update the incident response plan to ensure that it remains relevant and effective. This should be done in response to changes in the organization’s environment, such as new threats, technologies, or regulations.
- Communicate the plan. Ensure that all employees are aware of the incident response plan and their roles and responsibilities in executing it. This is possible through training, awareness campaigns, and regular communication.
- Implement the plan. Once the incident response plan is created, it must be agreed upon and actively implemented. Any aspect of the plan that is questioned during an active implementation can be reviewed and updated as necessary.
What are some common mistakes to avoid in incident response planning
There are several common mistakes to avoid in incident response planning.
- Failing to implement a response plan.
- Lacking an understanding of the organization’s environment.
- Working with the wrong vendors.
- Failing to test backups.
- Having incident response plans that are too detailed and lengthy, which can prevent timely incident resolution.
Proper preparation and planning are key to effective incident response. That’s why it is important to regularly review and update the incident response plan to ensure that it is effective and up-to-date.
Summary
A Cyber Incident Response is the process of responding to and managing a cybersecurity incident. It’s critical for business continuity.
The good news: you can hire experts for this. An Incident Response Retainer is a service agreement with a cybersecurity provider that allows organizations to get external help with cybersecurity incidents. It provides organizations with a structured form of expertise and support through a security partner, enabling them to respond quickly and effectively in the event of a cyber incident.
The specific nature and structure of an incident response retainer will vary according to the provider and the organization’s requirements. A good incident response retainer should be robust but flexible, providing proven services to enhance an organization’s long-term security posture.
Contact SalvageData experts 24/7 for help with your response plan or for emergency data recovery.













